Trusted by









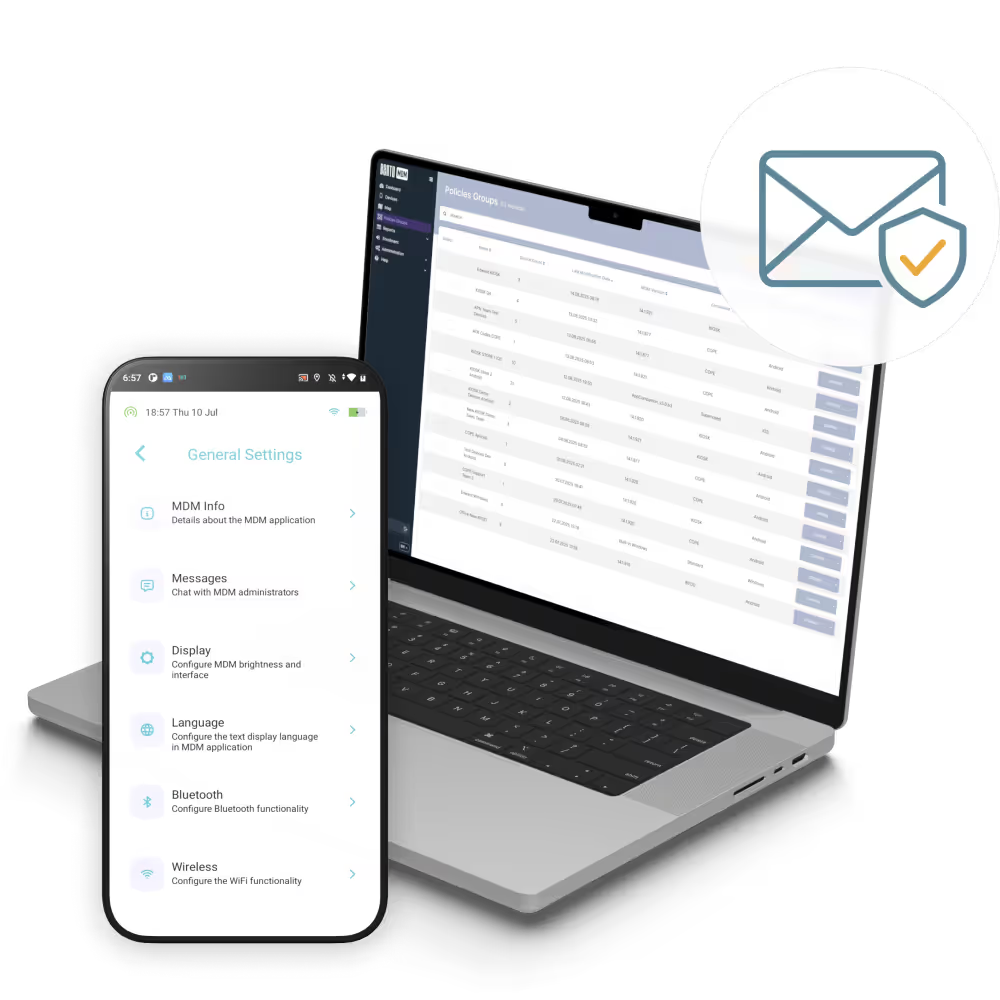
Email sync requires PIN, biometric, VPN, or location-based rules for security.
Email profiles auto-delete from non-compliant or lost devices, protecting sensitive data without manual steps.
Corporate messages are kept in a separate app container preventing data leakage and keeping personal communications private.
Corporate mail syncs only after device posture, OS, and encryption checks pass - maintaining secure email access.

All email access, profile deployments, and wipe events are centrally logged supporting compliance audits and forensic investigations.
Policies can block or encrypt attachments based on device role or location protecting sensitive files automatically.
Remote wipe targets only the corporate email container, preserving personal data while securing business communications.
Security controls, such as PIN, biometric authentication, VPN, or location rules, are enforced before syncing mail based on the environment's context.
Non-compliant or retired devices automatically lose their email profiles protecting sensitive data without manual intervention.
Corporate email resides in a managed container, that separates business data from personal apps and prevents data leakage.
Per-device certificates authenticate ActiveSync connections preventing shared credentials and enabling instant access revocation if a device is compromised.
Email only delivers when devices meet defined posture—OS version, encryption, and security policy checks occur first.

From BYOD to kiosk lockdown, Bento MDM secures and simplifies your device operations. Try it for free or book a live demo.


"With Bento MDM and FSM, we efficiently manage over 700 devices, automate workflows, and improve communication between field teams."
Cristian Bordescu
Operations Director



“Our collaboration with Bento on migrating over 2,000 DPD devices was exceptional. Their openness, flexibility, and constant support stood out throughout the project. Their quick adaptation to challenges and solution-oriented approach made all the difference, a truly reliable and professional partner.”
Valentina Ionescu
CIO, DPD
https://www.linkedin.com/in/valentina-ionescu-45a117bb
https://www.facebook.com/DPDRomania/
https://www.linkedin.com/company/dpd-romania/
https://www.dpd.com/
https://ro.wikipedia.org/wiki/DPD_Romania



"Bento Field Service Management and Mobile Device Management helped us streamline field interventions, secure mobile devices, and increase operational transparency."
Simona Gigiu
Business Line Director






Agency roles restrict access to classified applications, emails and devices providing tiered permissions for contractors, officials, and support staff with audit trails for accountability.


Plant operators and maintenance staff access machinery dashboards and logs based on their roles, preventing unauthorized control changes and ensuring operational safety compliance.


Field technicians receive role-specific permissions on rugged tablets enabling diagnostics and data entry without exposing unrelated device controls or settings.


Clinical teams can instantly access and troubleshoot patient tablets and monitors, avoiding critical care delays and minimizing on-site IT visits.





Is offline access possible?
Offline posture fails to block email while the device is disconnected. Once the devices reconnect and passes compliance verification, email profiles and cached messages are restored automatically.
How is security enforced?
Per-device PKI auth, posture checks, and isolated containers ensure that only compliant endpoints can securely access corporate email.
Can attachments be controlled?
Yes. Policies can block, encrypt, or restrict downloads and sharing of attachments based on device role or location.
How are profiles removed?
Email settings and containers are automatically deleted when policy violations occur, devices are lost, or when OS/encryption requirements fall out of compliance.
Which protocols are supported?
ActiveSync (Exchange), IMAP/SMTP, and native mail clients are supported, all integrating with PKI certificates for secure, conditional email delivery.
How is access granted?
Bento MDM pushes email profiles only after devices pass posture assessments. Non-compliant devices automatically lose both the profile and the secure email container.
What is conditional email access?
Email sync occurs only on devices that meet defined security policies – such as OS version, encryption, and compliance checks - before corporate mail is delivered.

From BYOD to kiosk lockdown, Bento MDM secures and simplifies your device operations. Try it for free or book a live demo.
