
Trusted by









Maintain policies, logs, and queued commands even when devices are offline.
Supports fleets of any size with distributed collectors and centralized analytics, maintaining performance and reliability as operations scale.
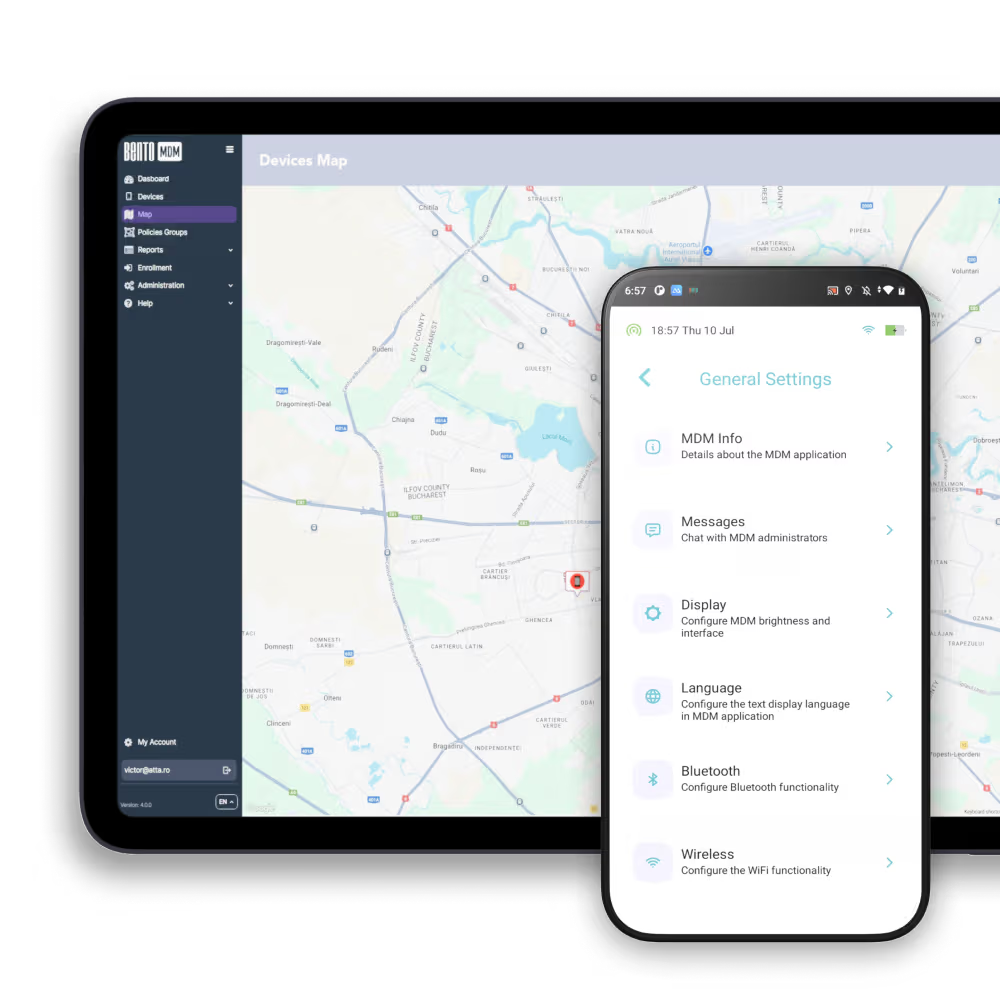
A single console displays security metrics, incident logs, and device statuses, streamlining monitoring and decision-making.

Interactive timeline views enable teams to investigate root causes,affected devices, and remediation steps for faster, more effective incident resolution.
Stream alert data and logs into SIEM platforms through secure connectors, enabling effective cross-source correlation and advanced threat hunting.
Automate the generation and delivery of compliance and health reports on a set schedule streamlining audit preparation and executive briefings.
Define thresholds for CPU spikes, storage limits, or failed updates with notifications routed to the appropriate teams via email or SMS.
Devices queue logs and health data locally when disconnected, syncing automatically upon reconnection to maintain continuous visibility.
Automated scans detect malware, unauthorized access, and signs of exploits, alerting teams before breaches can spread.
Policy violations trigger immediate notifications, helping teams fix configuration, patch, or encryption issues before they escalate and impact operations.
Live, interactive dashboards track CPU, memory, battery, storage, and network metrics, instantly highlighting anomalies for swift troubleshooting across devices.

From BYOD to kiosk lockdown, Bento MDM secures and simplifies your device operations. Try it for free or book a live demo.


"With Bento MDM and FSM, we efficiently manage over 700 devices, automate workflows, and improve communication between field teams."
Cristian Bordescu
Operations Director



“Our collaboration with Bento on migrating over 2,000 DPD devices was exceptional. Their openness, flexibility, and constant support stood out throughout the project. Their quick adaptation to challenges and solution-oriented approach made all the difference, a truly reliable and professional partner.”
Valentina Ionescu
CIO, DPD
https://www.linkedin.com/in/valentina-ionescu-45a117bb
https://www.facebook.com/DPDRomania/
https://www.linkedin.com/company/dpd-romania/
https://www.dpd.com/
https://ro.wikipedia.org/wiki/DPD_Romania



"Bento Field Service Management and Mobile Device Management helped us streamline field interventions, secure mobile devices, and increase operational transparency."
Simona Gigiu
Business Line Director






Across agencies, centralized dashboards surface compliance gaps, security incidents, and audit logs, supporting strict regulatory requirments and rapid incident response.


Anomaly detection alerts on industrial controllers and IoT sensors help prevent costly downtime and continuously enforce safety protocols.


Offline data queues and breach notifications sync upon reconnection, maintaining continuous monitoring of critical equipment on monitors and tablets.


In stores, compliance reports track POS and inventory scanners’ health, ensuring transaction security, uptime, and audit readiness without manual checks.


Dashboards highlight policy violations and offline tablets helping IT teams keep student devices secure and classrooms running smoothly.


In hospitals and clinics, real-time alerts flag unpatched devices and unauthorized access attempts—safeguarding PHI and ensuring HIPAA compliance.





How are reports delivered?
Reports and dashboards are accessible in the MDM console, with options to schedule email digests or export files for stakeholders.
How is compliance reporting handled?
Automated compliance dashboards track policy adherence, generate audit-ready summaries, and highlight non-compliant devices for rapid remediation.
Can Bento integrate with SIEM platforms?
Yes. Secure connectors and webhooks forward alerts and logs into SIEM tools, allowing cross-source correlation and advanced threat analysis.
Which security events are tracked?
Breach attempts, policy violations, OS update failures, malware signatures, and offline device statuses—all logged and surfaced in real time.
How does security reporting work?
Scheduled or on-demand reports aggregate compliance statuses, patch levels, and security events—exportable as PDFs or CSVs for audits and reviews.
What is MDM security monitoring?
Continuous tracking of device health, compliance, and threat indicators via centralized dashboards to help teams spot and address issues before they escalate.

From BYOD to kiosk lockdown, Bento MDM secures and simplifies your device operations. Try it for free or book a live demo.
