Trusted by









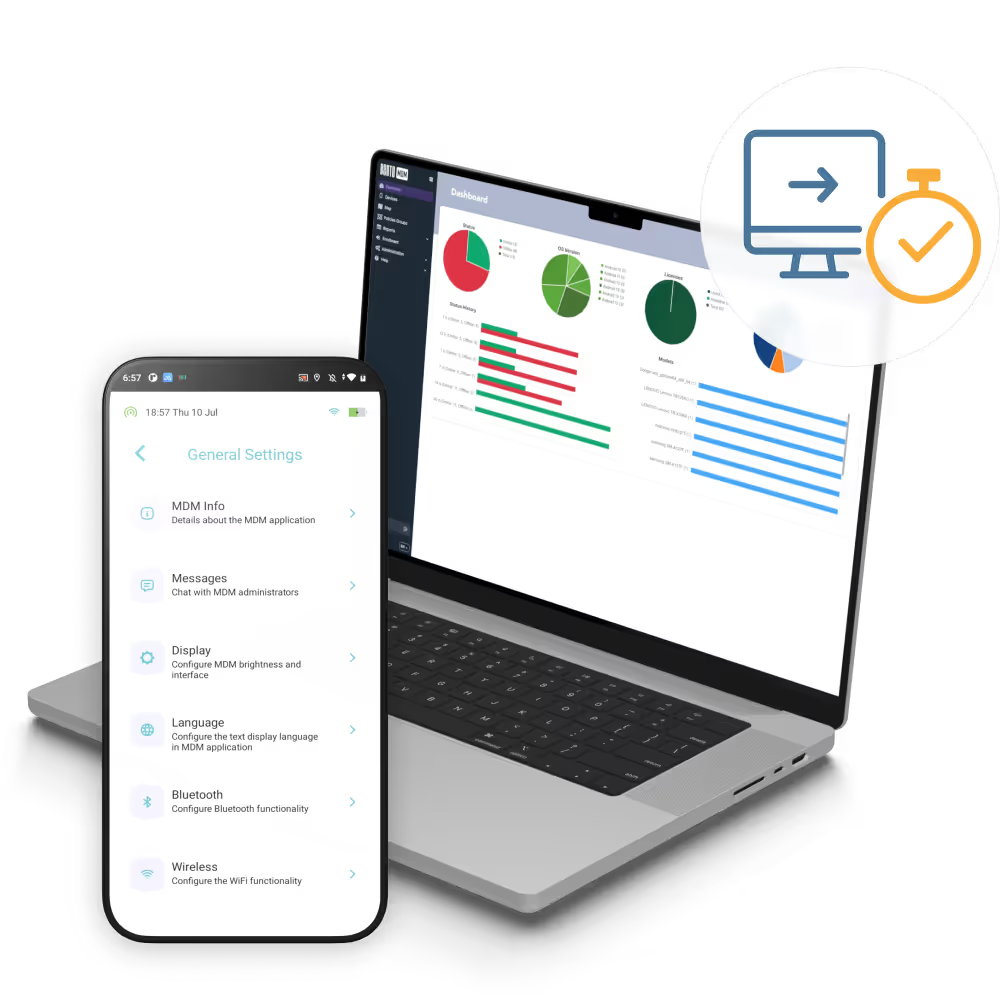
Access requests are approved via console or API on demand, allowing teams to initiate support sessions without manual setup delays.
Conditional checks verify device posture, compliance, and location to enforce zero-trust principles before access is granted.
Access windows open only when needed, and close automatically, eliminating standing privileges and reducing attack surfaces.

Provides granular admin permissions for safe BYOD support.
Session events automatically create or update tickets in existing ITSM platforms streamlining incident workflows and tracking.
Session records capture start and end times, user identities, and actions taken, aiding in forensic analysis and compliance.
All session traffic is encrypted end-to-end, protecting data during diagnostics, troubleshooting, or configuration tasks.
Connections terminate automatically at the scheduled end or on demand, preventing forgotten or abused access privileges.
Device posture, encryption status, and policy compliance are automatically validated before remote connections are granted.
Access scopes limit which device functions or apps are visible to support teams, ensuring they see only what’s required.
Sessions automatically expire after a defined duration, eliminating lingering permissions and minimizing the risk of unauthorized access.
Technicians request remote access through the console or API initiating secure connectionsonly when needed for support tasks.

From BYOD to kiosk lockdown, Bento MDM secures and simplifies your device operations. Try it for free or book a live demo.


"With Bento MDM and FSM, we efficiently manage over 700 devices, automate workflows, and improve communication between field teams."
Cristian Bordescu
Operations Director



“Our collaboration with Bento on migrating over 2,000 DPD devices was exceptional. Their openness, flexibility, and constant support stood out throughout the project. Their quick adaptation to challenges and solution-oriented approach made all the difference, a truly reliable and professional partner.”
Valentina Ionescu
CIO, DPD
https://www.linkedin.com/in/valentina-ionescu-45a117bb
https://www.facebook.com/DPDRomania/
https://www.linkedin.com/company/dpd-romania/
https://www.dpd.com/
https://ro.wikipedia.org/wiki/DPD_Romania



"Bento Field Service Management and Mobile Device Management helped us streamline field interventions, secure mobile devices, and increase operational transparency."
Simona Gigiu
Business Line Director






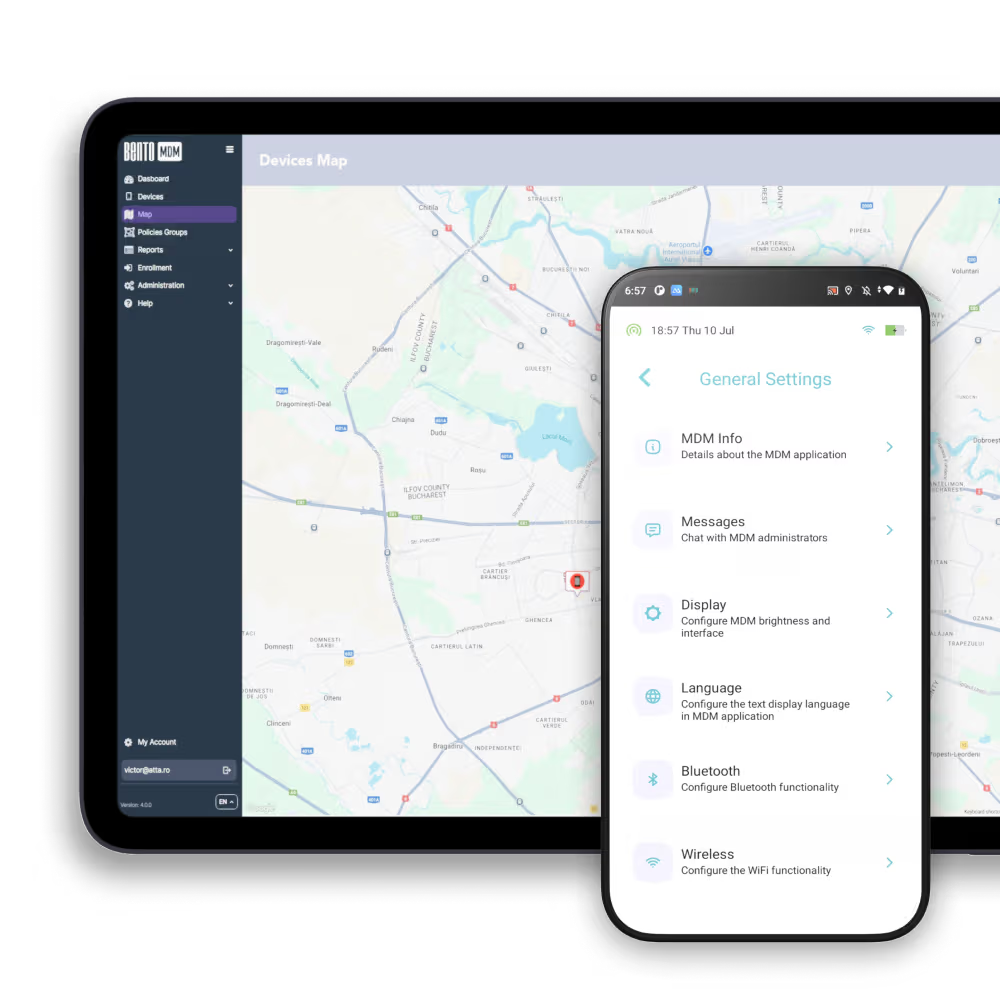
In government agencies, just-in-time remote access sessions secure classified devices, providing temporary support while enforcing zero-trust policies and maintaining audit trails.


Just-in-time remote access sessions secure device troubleshooting in remote locations, granting technicians temporary control and removing standing permissions.


On-demand remote sessions quickly resolve POS and inventory issues, enabling secure automated troubleshooting without requiring permanent access or interrupting customer service.


Time-limited remote sessions provide secure device control for maintenance, preventing unauthorized access and preserving continuity of patient care.





How are access logs maintained in MDM?
All session details – start/end times, user identities, and actions – are logged centrally for forensic review and compliance auditing.
Can JIT integrate with helpdesk systems?
Yes. Session events generate or update tickets via webhooks or REST APIs, streamlining incident tracking within existing ITSM workflows.
Is JIT remote access secure?
End-to-end encryption, zero-trust posture validation, and automated revocation ensure secure connections while minimizing attack surfaces.
Which devices support JIT access?
Smartphones, tablets, laptops, kiosks, and rugged endpoints enrolled in Bento MDM can receive time-limited remote support sessions.
How do access sessions start?
Support requests are initiated via the MDM console or API, triggering a time-bound connection once compliance and posture checks have passed.
What is just-in-time remote access?
Temporary, on-demand sessions grant support teams secure device access only when needed, automatically expiring to remove standing permissions.

From BYOD to kiosk lockdown, Bento MDM secures and simplifies your device operations. Try it for free or book a live demo.
