Trusted by









Nested roles and group inheritance simplify large deployments, adapting to organizational growth without cumbersome reconfiguration.
Default roles provide minimal access by design, limiting exposure and granting critical operation rights only when necessary.
Centralized role assignments eliminate redundant policies and maintain consistent access rules across devices, departments, and projects.
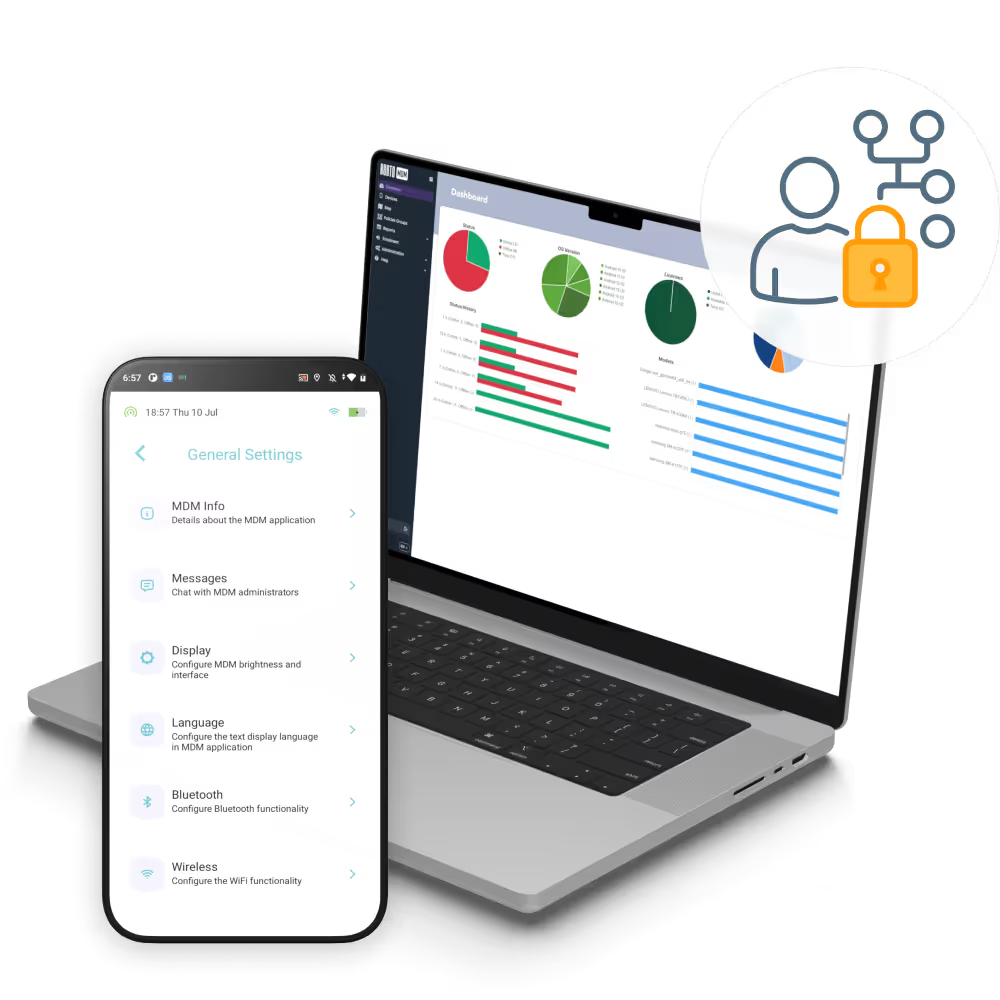
Role definitions assign precise permissions to device groups, so teams access only the resources and functions they need.

Role-based controls scale effortlessly across global fleets, consistently providing least-privilege as deployments grow without requiring cumbersome reconfiguration.
Comprehensive logs capture role changes, permission grants, and access attempts providing full traceability for compliance audits and security reviews.
Combine role assignments with device posture, location, or time-based conditions, dynamically adapting access to security and operational contexts.
Nested roles inherit permissions from parent roles, simplifying large deployments by reducing duplication and easing permission management.
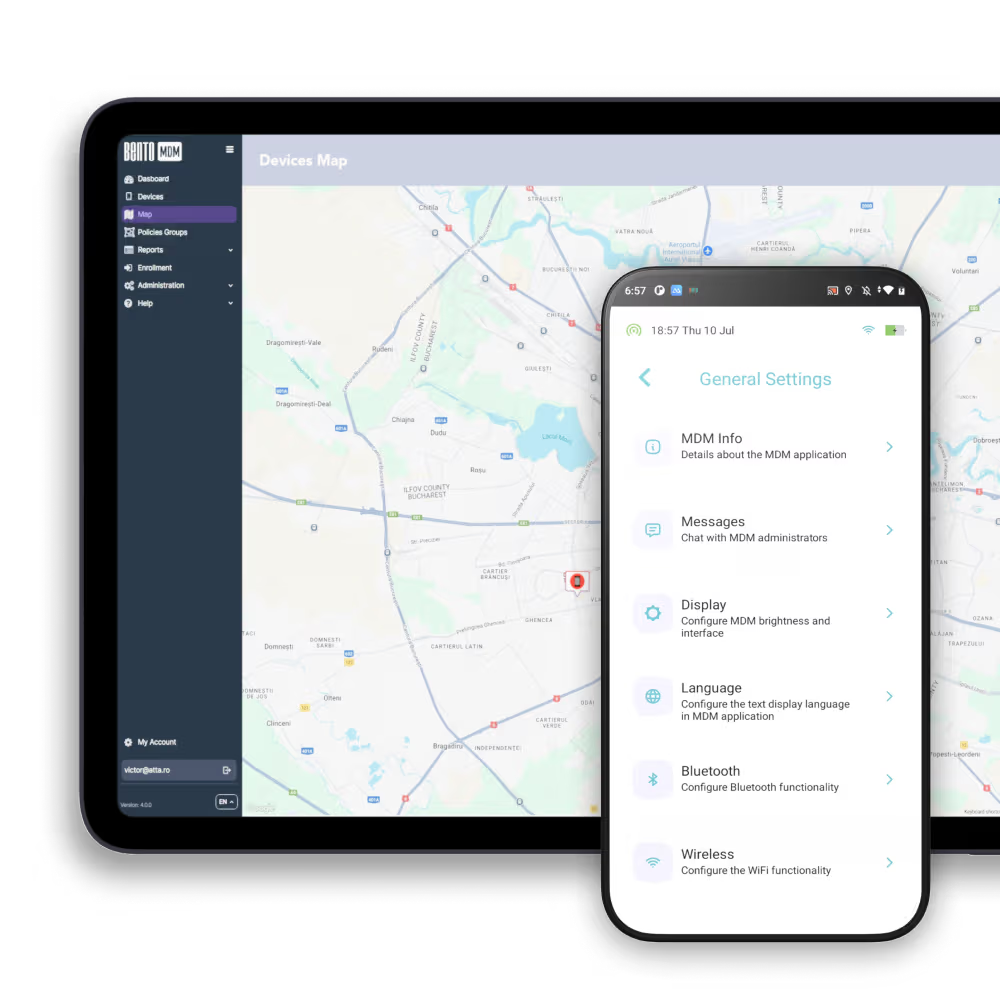
Apply roles to defined device groups (BYOD, kiosks, corporate-owned) ensuring that policies are enforced only on relevant endpoints without manual targeting.
Role memberships are automatically updated based on directory changes in Active Directory or LDAP, keeping access aligned with organizational shifts.
Bespoke roles are created with tailored permissions to support specific capabilities like app install, remote wipe, or policy changes per team needs.
Predefined role templates assign standard device permissions to job functions, such as Technician or Manager to speed up onboarding and ensuring consistency.

From BYOD to kiosk lockdown, Bento MDM secures and simplifies your device operations. Try it for free or book a live demo.


"With Bento MDM and FSM, we efficiently manage over 700 devices, automate workflows, and improve communication between field teams."
Cristian Bordescu
Operations Director



“Our collaboration with Bento on migrating over 2,000 DPD devices was exceptional. Their openness, flexibility, and constant support stood out throughout the project. Their quick adaptation to challenges and solution-oriented approach made all the difference, a truly reliable and professional partner.”
Valentina Ionescu
CIO, DPD
https://www.linkedin.com/in/valentina-ionescu-45a117bb
https://www.facebook.com/DPDRomania/
https://www.linkedin.com/company/dpd-romania/
https://www.dpd.com/
https://ro.wikipedia.org/wiki/DPD_Romania



"Bento Field Service Management and Mobile Device Management helped us streamline field interventions, secure mobile devices, and increase operational transparency."
Simona Gigiu
Business Line Director






Agency roles restrict access to classified applications, emails and devices providing tiered permissions for contractors, officials, and support staff, complet with audit trails.


Plant operators and maintenance staff access machinery dashboards and logs according to their roles, preventing unauthorized control changes and ensuring safety compliance.


Field technicians receive role-specific permissions on rugged tablets enabling diagnostics and data entry without exposing unrelated device controls or settings.


Cashier and manager roles control POS and inventory devices, restricting functions like price changes to authorized personnel only.


Teaching and admin roles unlock specified learning apps and reports, allowing students and staff to access appropriate resources securely.


Clinician roles grant access only to necessary patient-monitoring tablets and applications to protect PHI and reduce configuration errors.





Can roles apply to specific devices?
Absolutely. Roles target device groups (BYOD, kiosks, corporate) so policies and permissions execute only on relevant endpoints.
How does RBAC improve security?
By enforcing least privilege, RBAC limits exposure of critical functions to authorized roles only, reducing the risk of accidental or malicious actions.
What is role inheritance?
Nested roles inherit parent permissions to simplify large deployments by reducing duplicate configurations and easing permission management.
Can roles sync with directories?
Yes. Bento integrates with Active Directory/LDAP to auto-update role memberships as staff move teams, keeping access aligned with org changes.
How are roles created?
Define roles in the MDM console with specific permissions (lock, wipe, app install) and map them to user groups or devices.
What is RBAC in MDM?
RBAC assigns device management permissions based on roles, departments, or device groups to ensure least-privilege access per team responsibilities.

From BYOD to kiosk lockdown, Bento MDM secures and simplifies your device operations. Try it for free or book a live demo.
