
Trusted by









Single Sign-On (SSO) portal cuts password fatigue and streamline user access.
MFA and adaptive and adaptive policies prevent unauthorized access.
Conditional accessrules adjust adapt by basedon device health, time, or location.
Comprenhensive authentication logs ensure visibility and compliance reporting.

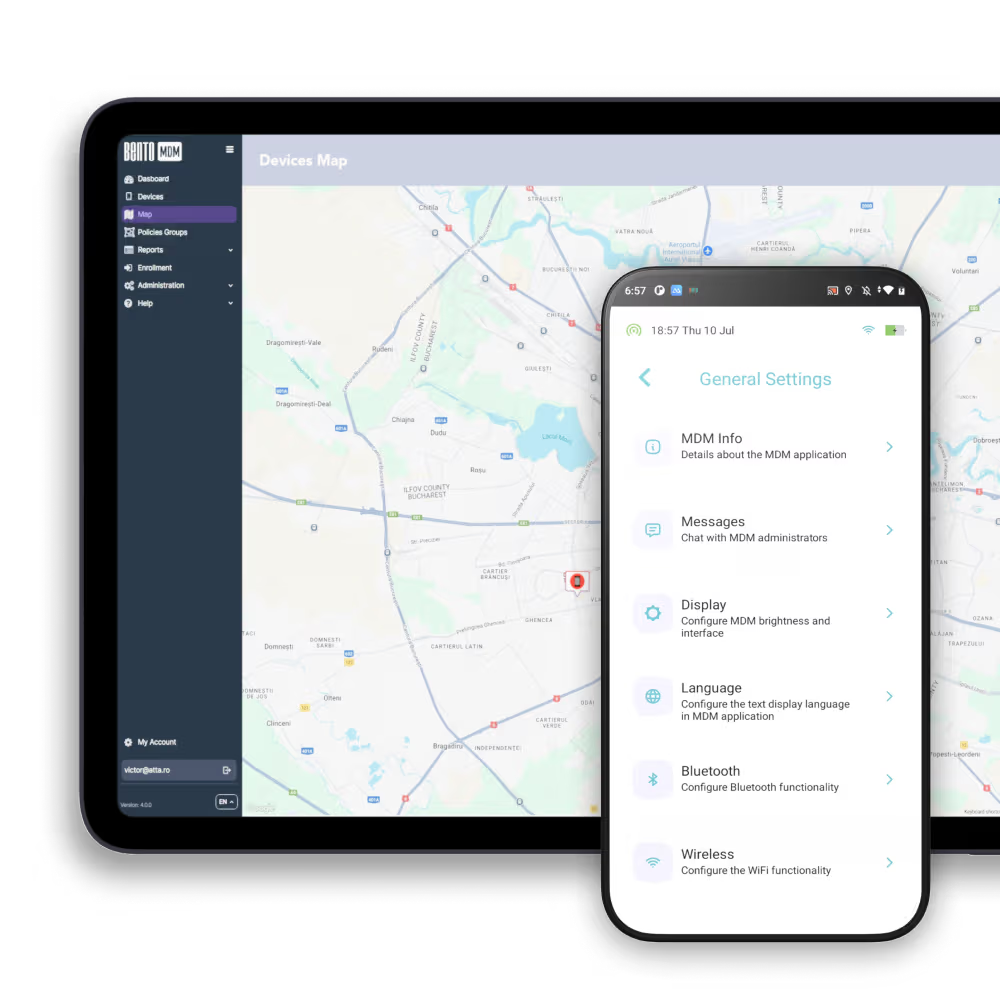
Unify user access through a centralized portal that simplifies authentication across all apps and devices using Bento MDM’s integrated SSO gateway.
Add a secure second factor without friction using SMS, TOTP, or push notifications, all enforced through Bento MDM’s adaptive policy engine.
Assigns permissions by role or group to provideleast-privilege access across every endpoint rmanaged by Bento MDM.
Automate access decisions based on location, device health, or time, applied dynamically through Bento MDM’s zero-trust policy framework.
Capture every login event with full context and generate compliance-ready reports instantly through Bento MDM’s unified audit console.
Sync users and groups with LDAP, Active Directory, and cloud identity providers through Bento MDM’s secure REST API integrations.

Real-time posture checks, adaptive MFA, and one-click compliance evidence for HIPAA/GDPR and PCI.

Adjust authentication requirements in real time based on device posture, IP reputation, or unusual user behavior.
Use PKI certificates to establish trust, eliminate weak passwords, and secure access to sensitive applications.
Automatically log out idle sessions, require re-authentication at set intervals, and prevent credential hijacking from inactive users.
Grant time-boxed admin rights only when needed, with full audit trails to eliminate persistent privileges.
Track IAM policies, MFA enrollment, and access attempts in real time with exportable audit logs and reports.
Monitor IAM policies, MFA adoption, and access attempts in real time, with exportable audit logs.
Integrate with SIEM, ITSM, and incident response platforms to extend identity signals intowider security workflows.
Apply secure, conditional access rules even when devices are offline, syncing posture and events once they reconnect.



"With Bento MDM and FSM, we efficiently manage over 700 devices, automate workflows, and improve communication between field teams."
Cristian Bordescu
Operations Director



“Our collaboration with Bento on migrating over 2,000 DPD devices was exceptional. Their openness, flexibility, and constant support stood out throughout the project. Their quick adaptation to challenges and solution-oriented approach made all the difference, a truly reliable and professional partner.”
Valentina Ionescu
CIO, DPD
https://www.linkedin.com/in/valentina-ionescu-45a117bb
https://www.facebook.com/DPDRomania/
https://www.linkedin.com/company/dpd-romania/
https://www.dpd.com/
https://ro.wikipedia.org/wiki/DPD_Romania



"Bento Field Service Management and Mobile Device Management helped us streamline field interventions, secure mobile devices, and increase operational transparency."
Simona Gigiu
Business Line Director








Isolate corporate apps within secure containers on employee-owned devices.


Provide temporary, time-bound credentials for secure access on shared devices.


Assign and audit elevated rights dynamically to maintain full administrative accountability.


Protect distributed teams with secure Signle Sign-On (SSO) and adaptive MFA protect for every login.


Grant scoped, expiring permissions to third-party users, ensuring least-privilege access at all times.


Time-limited overrides allow critical staff to bypass policies securely when needed.



What is an Identity and Access Management (IAM) solution?
An IAM solutions centralizes authentication, authorization, and user provisioning across applications and devices, streamlining secure access.
What is enterprise identity and access management used for?
IT manages user identities, enforcing policies, and controls authentification acrossa BYOD, remote work, and regulated environments.
How does an IAM solution support BYOD?
It separates corporate and personal profiles, applies secure work-container policies, and preserves user privacy on personal devices.
What is Single Sign-On (SSO)?
SSO enables users to log in once and gain to access multiple applications without reentering credentials.
How do conditional access policies work?
These policies dynamically adjust access rules based on factors like device health, user role, location, or time of day.
What is role-based access control (RBAC)?
RBAC assigns permissions to users based on their job roles, ensuring each person has only the access they need.
Why implement multi-factor authentication (MFA)?
MFA adds extra verification layers such as push notifications, SMS codes, or TOTP to reduce the risk of unauthorized access.
How does IAM integrate with identity providers?
It connects through SAML, OAuth, or REST APIs to systems like LDAP, Active Directory, and cloud identity services for seamless user synchronization.

Manage every phone, tablet, and workstation from one console—across healthcare and beyond—with Bento MDM.
